To date, there have been a number of simulated, experimental, and real-world cyber-attacks on unmanned aerial systems (UAS). These attacks have been carried out by different actors including researchers, militaries, rogue hackers, and unidentified sources [1]. Successful cyber-intrusions on aircraft are often considered incredibly dangerous because they could, hypothetically, control the vehicle once inside. However, there have been few attempts to do so and successful attacks have only been able to partially control the vehicle, moderately at best.
What we have learned from these attacks is that the issue of installing malware on a UAS has been proven to be a solved problem. While there are known safeguards to prevent the installation of malware onto a system, it is mostly a matter of operational security at this point. Furthermore, while a cyber-attack on a UAS could take full control of a vehicle, in theory, no such attempts have been made and the feasibility of such an attack remains unknown. In short, we don’t know whether or not it’s possible to hijack a UAS via cyber-attack.
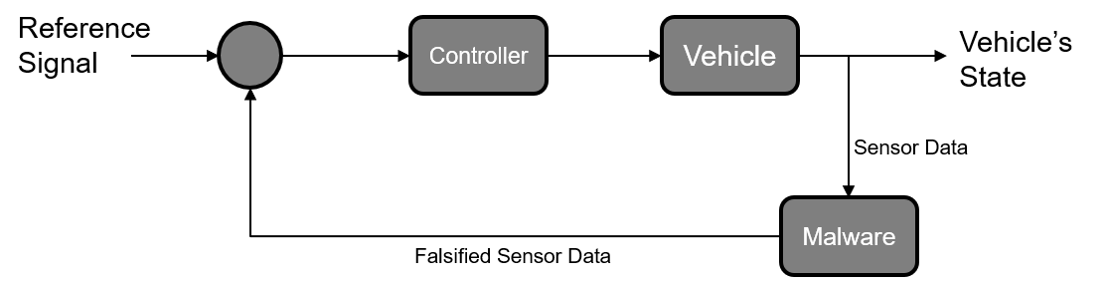
This research will investigate the possibility of taking full control of a UAS via a malware program installed on the flight computer and will identify safeguards to defend against such an attack. This malware will make use of a novel algorithm designed to manipulate the control of the vehicle by intercepting and modifying the sensor data. The malware will alter the sensor data to fool the controllers into performing the actions desired by the malware. Furthermore, this attack has potential to be used remotely via the use of sensor spoofing technology.
The objectives of this research are:
- Investigate the possibility of controlling a UAS via installed malware by altering the sensor data.
- Assess the feasibility and seriousness of such an attack.
- Investigate the possibility of performing the attack remotely with sensor spoofing.
- Develop a method of defense against this attack.
Methods
Installing malware onto a UAS is a solved problem and is not the focus of this research. Instead, for the purposes of this research, we will assume that the malware already has access to the system. We can break up the investigation into the research of both an onboard and remote attack. Additionally, sensor data can be broken up into two categories: structured and unstructured. Structured data, such as GPS location or bank angle, is much more well-defined and provides a simpler model to work with compared to unstructured data, such as image data.
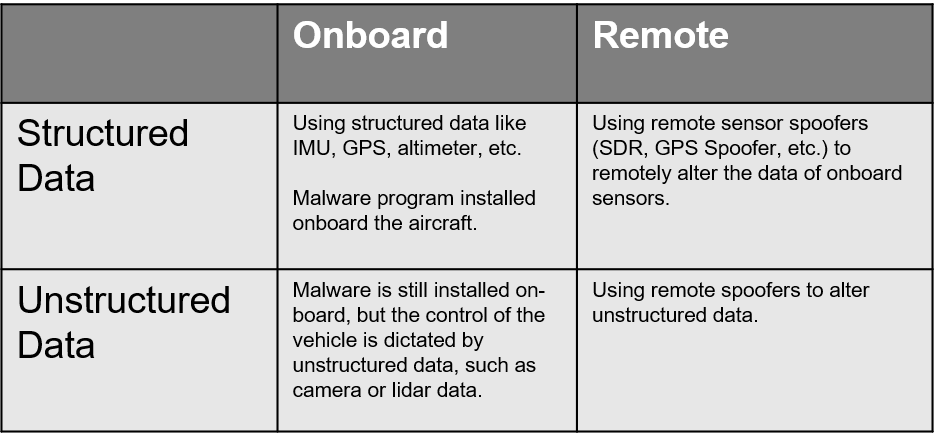
Thus, the first phase will be to perform an onboard attack on a controller which runs purely on structured data. In this phase, traditional controls techniques will likely prove as a well-working solution.
In the second phase, we can begin to investigate onboard attacks on unstructured data. Often, good control performance with unstructured data relies on machine learning and optimal control techniques which are likely good candidates for this problem.
Finally, in the third phase we can begin to look at remote attacks. It is likely that this remote attack may remain only theoretical and reliant on the development of new spoofing techniques. However, the algorithm should still be evaluated to assess its ability to perform despite the error introduced by estimation and spoofing tools.
Working with me on this project are:
Graduate Students:
-Garrett Jares , Ph.D. AERO
This material is based upon work supported by the National Science Foundation Graduate Research Fellowship Program under Grant No. DGE:1746932. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation.